Our very own security specialist, Richard Den Houdijker, shared his point of view on the recent developments regarding VPAM – Vendor Privileged Access Management. Most people might already have heard of ‘Imprivata’, especially in the world of healthcare. Or the Single-Sign-On principle where you authenticate your identity with a badge on your computer. Today we’re going a step further. Let’s focus on the protection of such accounts. Let’s take a look at what was shared during the Healthcare Colloquium event.
Even the Pentagon was at risk
When we talk about ‘privileged accounts’ and ‘privileged access’, the word ‘privileged’ comes around. When we take a look at third parties vendors who have to use our privileged accounts to help or support us, how can we be sure that those privileged accounts and accesses are protected or secured?
Did you know that almost half of all companies in the past 12 months had to deal with a breach that was a result of an account that was assigned to third party companies or vendors?

“A few years ago, there was a breach in the Pentagon because of the exact same reason. You see, even the biggest powers or the most important organizations can be affected by that.”
Richard Den Houdijker, IAM & PAM Security Specialist
No structure could cause a big mess
But why is it so difficult to protect and secure those accounts? Companies don’t really have a standardized way of dealing with access to their system by third party vendors. Just think about it, how often do you get the question to “quickly” help through Teamviewer or in a Teams call when screens are being shared. You might actually have no idea of all the identities that are created on your systems.
Next to that, there’s also something that is called “inactive management” or vendor identities/lifecycle management. Do you have an overview of all your third-party vendors? All the companies that help you? What accounts they have and what they’re all doing? That’s easier said than done.
Last but not least, there’s actually no visibility or control once they have access in that environment. Do you know what those individuals are doing in your environment?
Those are all pain points that could be solved by one simple solution: Vendor Privileged Access Management.
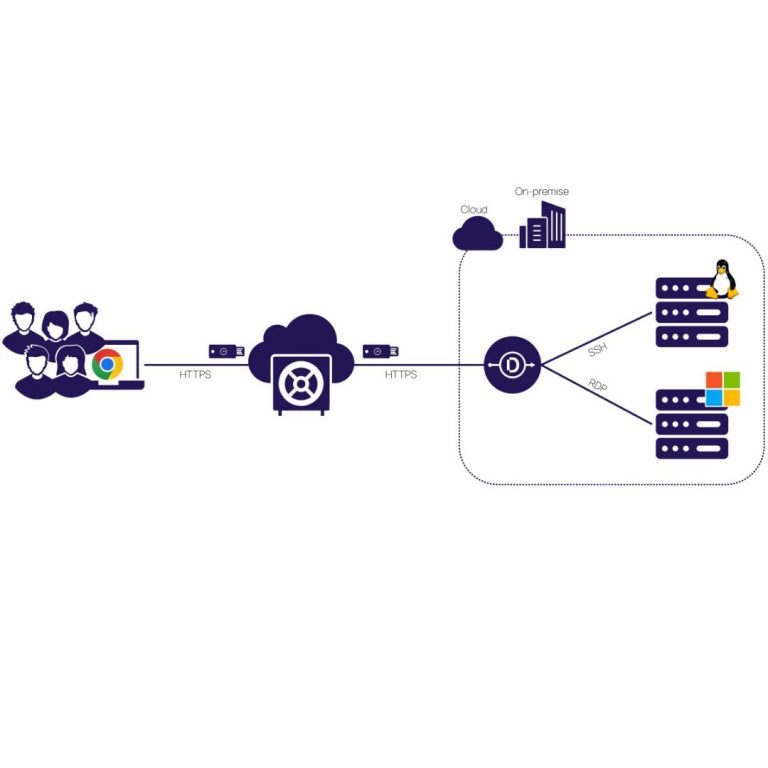
It’s essential but shouldn’t be a vulnerability
To sum up: vendor access might be essential, but it doesn’t have to be a vulnerability. Vendor Privileged Access Management offers the structure, visibility, and control needed to protect your organization from breaches caused by third-party access. In our next blog, we’ll dive into the core capabilities of a solid Vendor Privileged Access Management solution and how they can be tailored to your needs. Stay tuned!
Curious about how Vendor Privileged Access Management could strengthen your security strategy? Get in touch, we’re happy to help you discover the possibilities


